Let’s Encrypt is a movement. It is a nonprofit Certificate Authority providing TLS certificates to over 225 million websites. These are first-class, standards-compliant digital certs that can be used for any number of domains (and sub-domains), for free.
So, imagine being able to immediately “issue” these certificates, with just one click, and use them with your websites (using WebMon) or mail servers (using MailServe) — again, with just one click. Now you can.
Introduction
This is the Letsencrypt Enabler window.
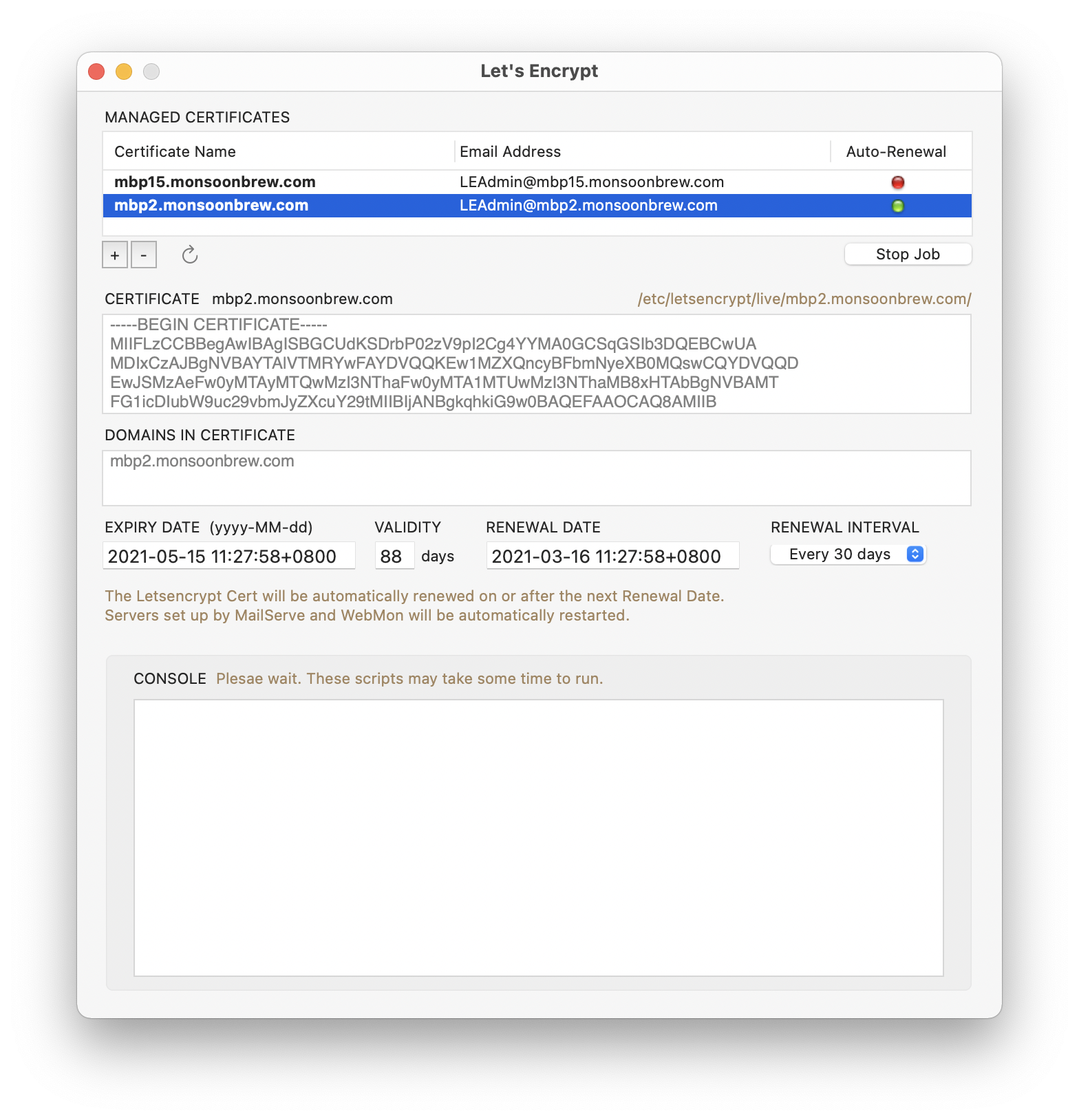
When you start up, you will have no certificates, of course. Letsencrypt Enabler installs all the stuff you need to generate Let’s Encrypt certificates into /opt/homebrew-cutedge. The certifcates that are generated are saved into /etc/letsencrypt/live, where MailServe and WebMon can find them.
NOTE : unlike earlier versions of Letsencrypt Enabler, which requires you to install Xcode Command Line Tools, Homebrew and Let’s Encrypt’s Certbot manually (and very slowly, thorugh clicking three buttons, and the final result is spread out all over /usr/local), version 2.0.2 for Big Sur onwards installs a pre-built (ARM or Intel) version of Certbot into the single folder /opt/homebrew-cutedge, which makes it very easy to un-install.
Creating your first certificate
Look for the + button near the top left of the window, amd click on it. Enter your domain name. Then click OK. That’s it.
PS: new in version 2.0.4 — Option-click on the OK button to do a dry-run without actually creating the cert. The Console log will show if the cert could be created or, if not, what the errors are.
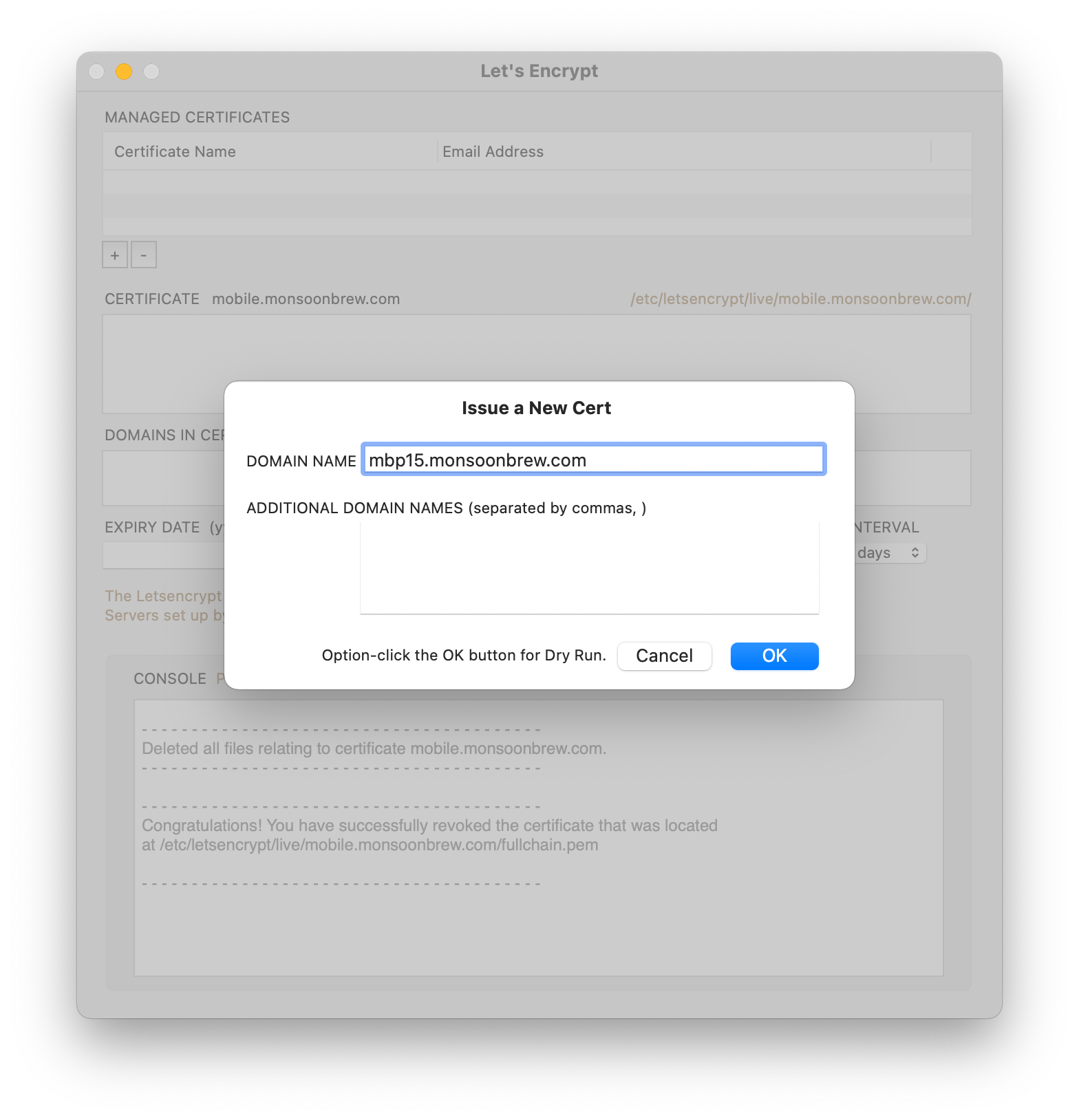
You can create any number of certs. Or include any number of domains and sub-domains in one cert (use the ADDITIONAL DOMAIN NAMES field).
Once these are created, you can use them with your mail and web servers. Both MailServe and WebMon have a radio button for turning on SSL using Let’s Encrypt certificates. The only requirement being that the Domain Name must “line up”, remain consistent, across all three applications.
When you see an error in the Console field while creating a cert
If you can’t create a Let’s Encrypt certificate, you may have a problem with the Domain Name System.
Let’s Encrypt’s Certbot communicates with its parent servers by running a builtin standalone server on port 80. So, if you have a web server running, you need to shut it down temporarily for Certbot to do its job.
Let’s Encrypt’s server will try to communicate with Certbot’s builtin web server, using the domain names you supplied in your cert request. If it can do that, it will accept that as proof that you own those domain names and have the right to control the services on the machine associated with them.
(WebMon user note : Letsencrypt Enabler shuts down the Apache server enabled by WebMon automatically. Then brings it up when it’s done.)
If all these line up, you’ll have the pleasure of seeing your first free, first class, digital cert being created.
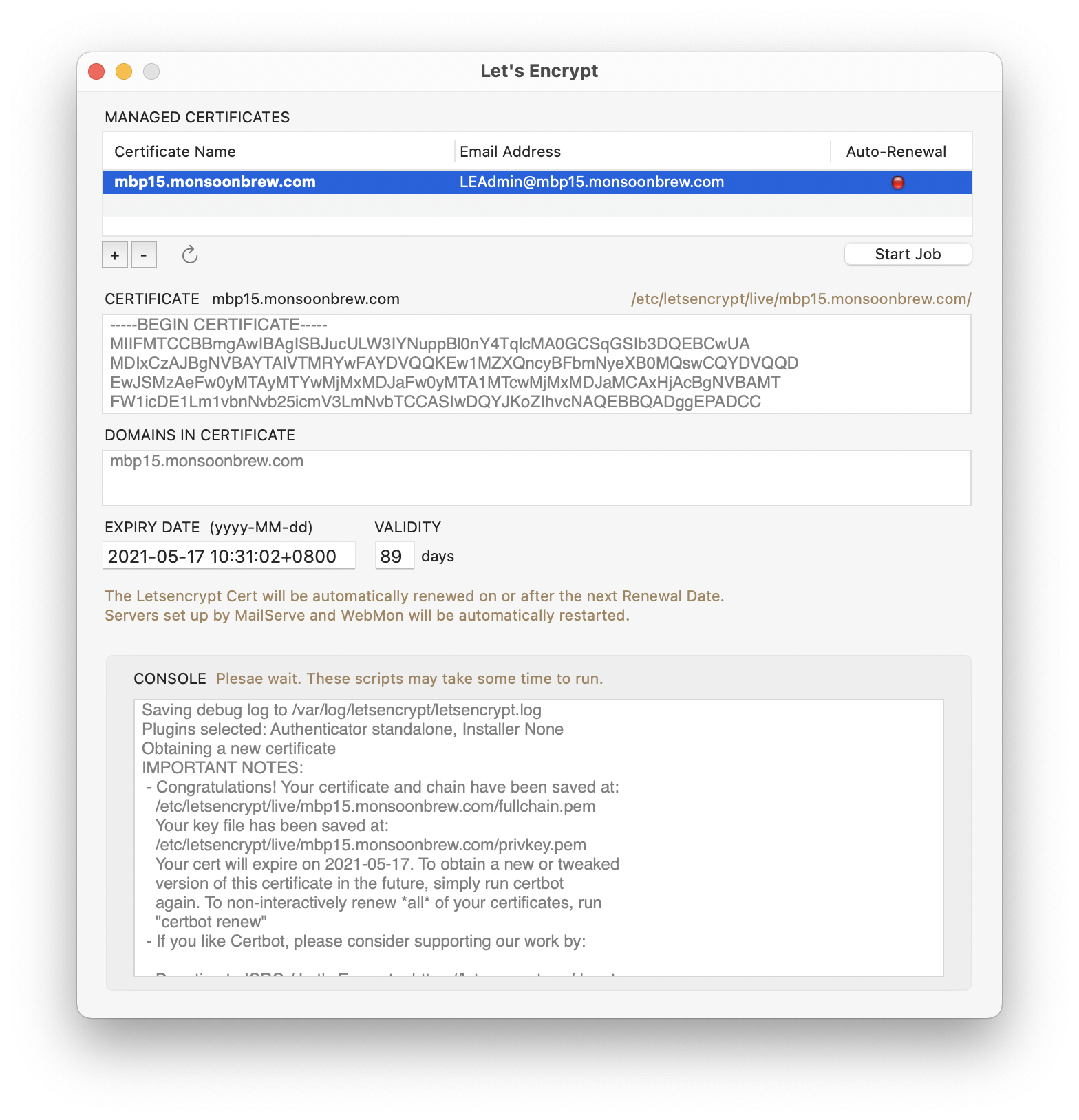
Automated Cert Renewals
There is a pain to using Let’s Encrypt certificates — they have very short validity periods. Most users renew them at the 60 day mark.
Letsencrypt Enabler makes the renewal process painless. Under the Auto-Renewal column, you can click the Start Job button to start a periodic job that will talk to Let’s Encrypt’s servers at the specifed time intervals. The default renewal interval is 60 days.
You can set the Renewal Interval in Letsencrypt Enabler. Choose a smaller one, say two hours, or one day, to test that the automated cert renewal works. Choose the Interval setting and then quit the app. Just set and forget.
NOTE : but do note that Let’s Encrypt has a hard limit of 5 updates allowed each week. Don’t cross that or your domain will be temporarily banned from making renewals.
Use the website https://crt.sh to check if your cert has been successfully renewed.
Letsencrypt Enabler’s periodic job will also tell WebMon and MailServe to automatically reboot your web and mail servers to make use of the renewed certs.
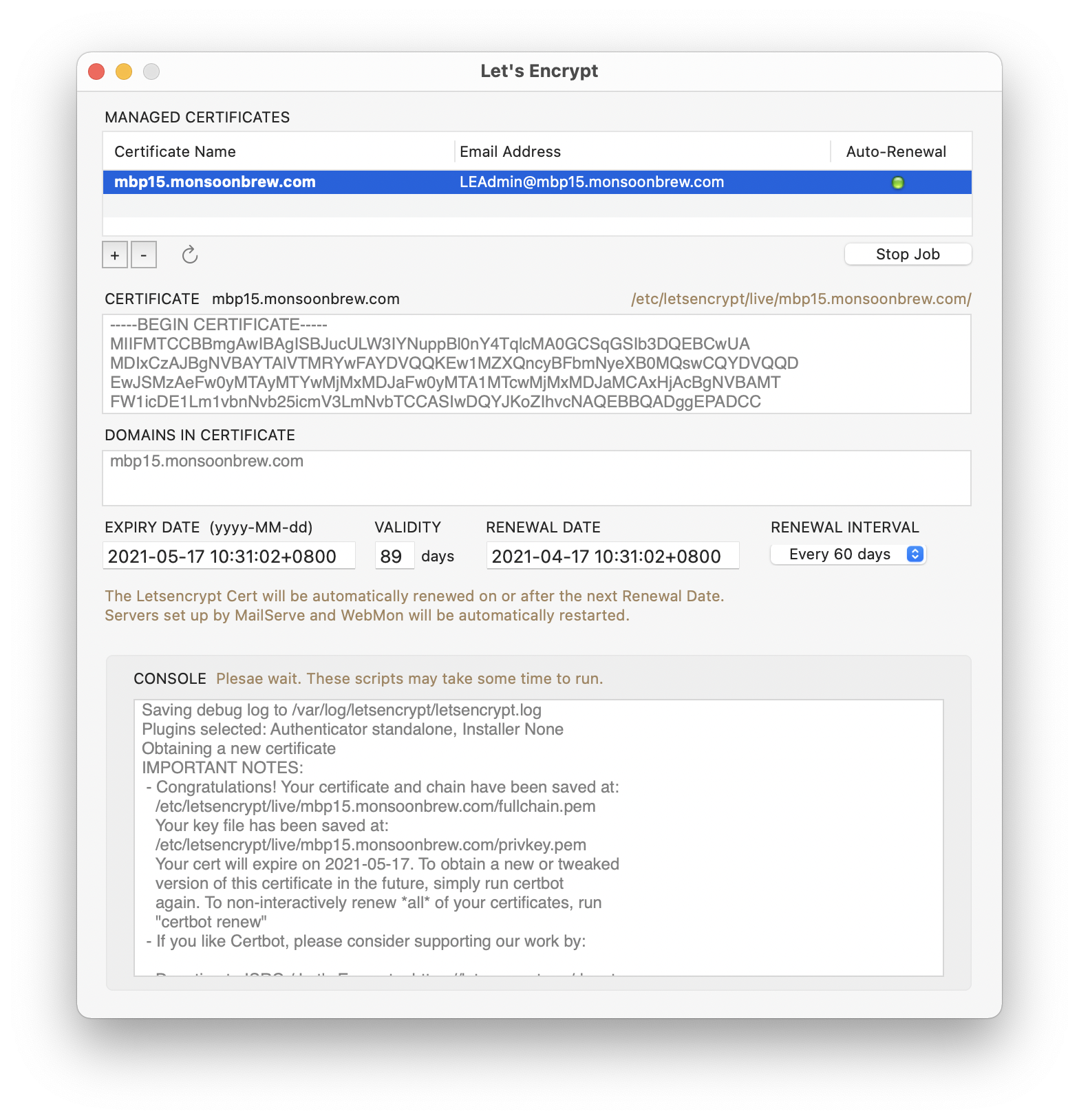
NOTE : If you set a Renewal Interval, it doesn’t mean that the renewal job will run exactly at the time stated in the Renewal Date field. For Renewal Intervals of less than a day, the periodic job is set to run every hour. For Renewal Intervals of a day or more, the periodic job is set to run only twice a day. Each time it runs, it checks to see if the current time is greater than the stated Renewal Date & Time. If it is, it does the renewal job of refreshing the current cert and rebooting the web and mail servers (if they’re set up by my other Enabler apps) to use the new cert.
This process will, of course, extend the new cert Expiry Date to the next 90 days and the Renewal Date to the next Renewal Interval. Once you’re sure everything is working correctly, set the Renewal Interval to 60 days and quit the app. The peridoc job will keep on running, until you revoke and delete the cert or un-install Letsencrypt Enabler.
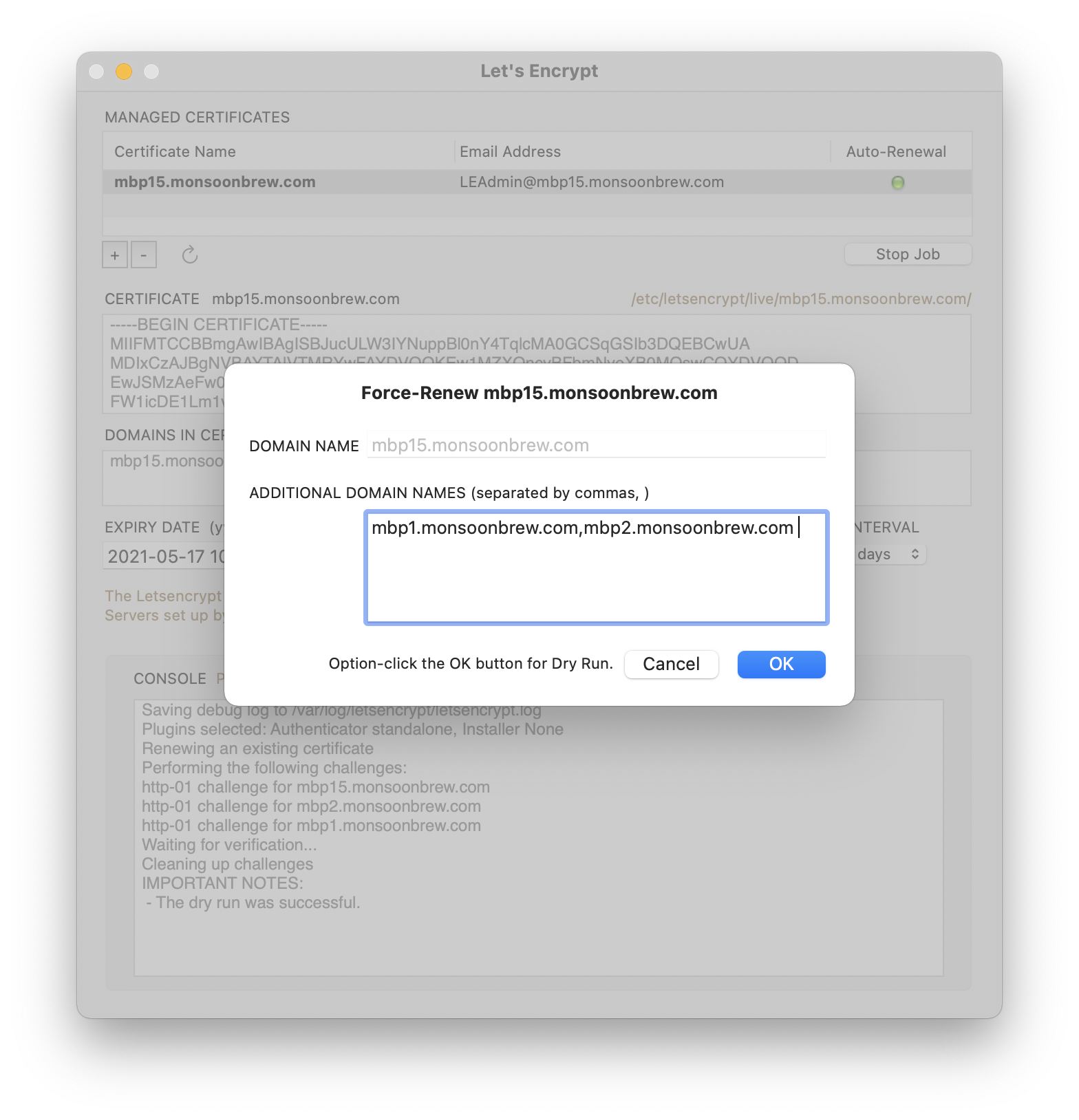
Updating the Letsencrypt Cert with a new set of domains
If you double-click on a cert record in the Managed Certificates table view, it will open up a dialog box where you can change the additional doman names included with this cert. You can use this cert wherever these domain names are used (with the proviso that ALL these domain names must point to the server you are running Letsencrypt Enabler on).
Option-click on the OK button to do a dry-run.
Revoking the Letsencrypt Cert
To Revoke a Cert, click the Revoke button (the - sign button under the Managed Certificates table view). Note the alert in the dialog box. There is no dry-run for this action. Clicking OK will completely delete this cert from your system (as well as Letsencrypt’s).

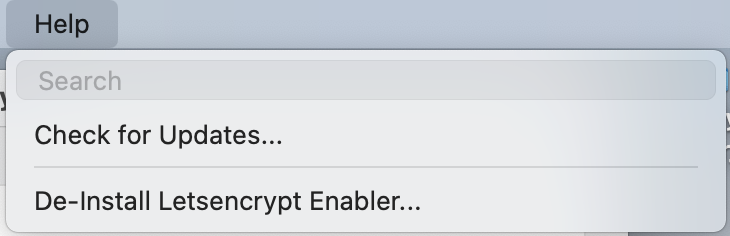
De-Installing Letsencrypt Enabler
You can un-install Letsencrypt Enabler by using the last menu item in the Help menu. It will shut down the Letsencrypt Enabler daemon, if it is running, and remove all files installed by Letsencrypt Enabler (in /opt/homebrew-cutedge). It will also revoke and remove all the certificates, if any, in /etc/letsencrypt/live.
Enjoy!
Release Log
2.0.2 November 20th 2020. This is the first version to include a pre-built /opt/homebrew-cutedge folder (in ARM or Intel versions), as appropriate to the running machine. There are symlinks to brew and certbot in /opt/homebrew-cutedge from /usr/local/bin, to keep compatibility with earlier versions of Letsencrypt Enabler, but the symlinks are not used by version 2.0.2 of Letsencrypt Enabler, at all, so that Letsencrypt Enabler’s use of Homebrew will have no impact on existing usage.
Note : to uninstall the version of Homebrew installed by earlier versions of Letsencrypt Enabler in /usr/local, do this in Terminal :
sudo /bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/uninstall.sh)"
2.0.3 November 21st 2020. Updated to work in Dark Mode.
2.0.4 February 16th 2021. This version improves on the basic features of the first version. Now the user can start or stop an automated cert renewal job, check the status to see if the job is running and start it if it is not running. The user can now modify a cert, adding to or removing domain names from the cert by double-clicking on a cert record to bring up a dialog box to make the modifications. And, very useful for debugging, the user can now do a dry-run when they're creating or modifying a cert. Just Option-click on the OK button to tell the app that this should be a dry-run. The Console log will show if the cert will be created correctly.
2.0.5 March 7th 2021. I tried to drop the —agree-tos parameter (together with the need for an email address) in calls to certbot in version 2.0.4 but it seems that this is a required parameter for registering new domains with Letsencrypt’s servers. This version puts it back.
The latest version is 2.0.5
This is a Universal "fat binary”, which will install HomeBrew and Letsencrypt Certbot in /opt/homebrew-cutedge in either ARM or Intel versions.
Please check out the Release Log
Contact
Bernard Teo